According to LastPass, one of the best password managers, hackers got access to a lot of customer personal information, encrypted and cryptographically hashed passwords, and other data in customer vaults.
The disclosure, which was made public on Thursday, the 29th of December, is a significant update to a breach that LastPass made public back in August. The company stated at the time that a threat actor gained unauthorized access to portions of the development environment for the password manager through a single compromised developer account and "took portions of source code and some proprietary LastPass technical information." Master passwords, encrypted passwords, personal information, and other data stored in customer accounts, the company claimed at the time, were unaffected.
Both Encrypted and Unencrypted Copies of Sensitive Data
According to the company's update on the 29th of December, hackers gained access to customer personal information and related metadata, such as billing addresses, email addresses, phone numbers, and IP addresses used by customers to access LastPass services. In addition, the intruders copied a backup of customer vault data that contained both encrypted and unencrypted data fields, such as website usernames and passwords, secure notes, and data from forms.
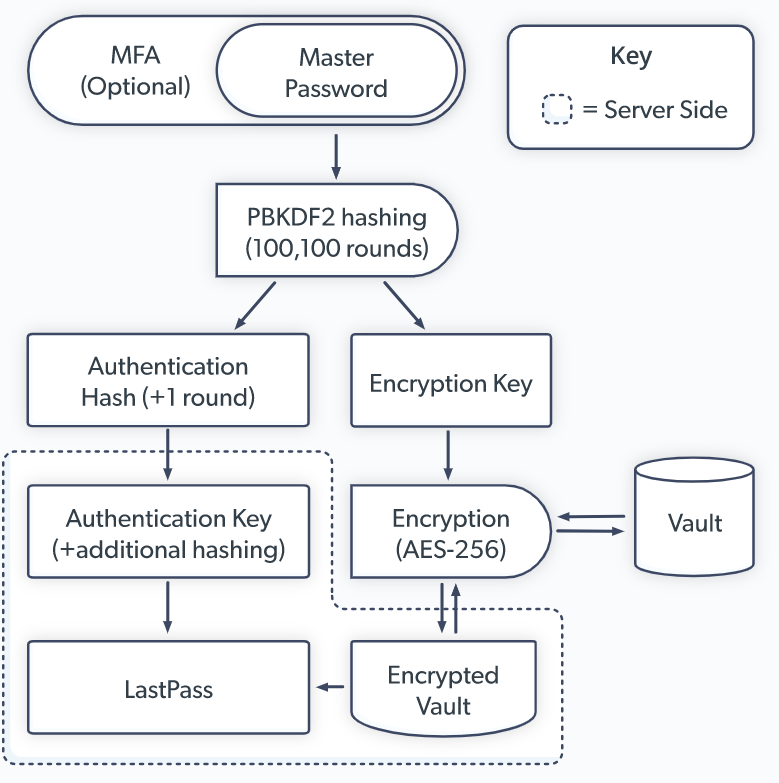
LastPass CEO Karim Toubba wrote, "These encrypted fields remain secured with 256-bit AES encryption and can only be decrypted with a unique encryption key derived from each user's master password using our Zero Knowledge architecture." He was referring to the Advanced Encryption Scheme as well as the fact that its bit rate is regarded as being one of the strongest in the industry. Storage systems that cannot be decrypted by the service provider are referred to as Zero Knowledge. The CEO went on to say:
As a reminder, LastPass has no knowledge of the master password and does not store or maintain it. The data is only encrypted and decrypted on the local LastPass client. Please refer to this page for additional details regarding our Zero Knowledge architecture and encryption algorithms.
It appears that a separate breach of Twilio, a San Francisco-based provider of two-factor authentication and communication services, is related to the intrusion that was made public in August and enabled hackers to steal the source code for LastPass as well as proprietary technical information. In that breach, the threat actor took data from 163 Twilio customers. At least 136 other businesses, including LastPass, were also breached by the same phishers that broke into Twilio.
The threat actor could use the stolen source code and technical information to hack a different LastPass employee and obtain security credentials and keys for accessing and decrypting storage volumes within the company's cloud-based storage service, according to the update on Thursday.
Toubba stated,
To date, we have determined that the threat actor copied information from backup that contained basic customer account information and related metadata, including company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service
after obtaining the cloud storage access key and dual storage container decryption keys. Additionally, the threat actor was able to copy a backup of customer vault data from the encrypted storage container, which is stored in a proprietary binary format and contains both fully encrypted sensitive fields, such as website usernames and passwords, secure notes, and form-filled data, as well as unencrypted data like website URLs.
An email asking how many customers had their data copied was not answered by LastPass representatives.
Protect Yourself Right Now
In addition, several measures LastPass has taken to strengthen its security following the breach were listed in Thursday's update. Retaining a managed endpoint detection and response service, decommissioning the hacked development, and rotating all relevant credentials and certificates that may have been affected are the steps.
It is alarming that such a wide range of personal information was obtained considering the sensitive nature of the data stored by LastPass. The fact that the threat actor now controls user vaults is also troubling. Given the threat actor's methodical and resourceful approach, cracking the password hashes is not out of the question, despite the fact that it would require a significant amount of resources.
Customers of LastPass should check to see that they have changed both their master password and all of the passwords in their vault. They should also check to see that they are using settings that are different from LastPass's default. Those settings use the Password-Based Key Derivation Function (PBKDF2), a hashing scheme that can make long, unique, and random master passwords impossible to crack, to hash stored passwords. The 310,000-iteration threshold that OWASP recommends for PBKDF2 in conjunction with LastPass's SHA256 hashing algorithm is woefully absent from the 100,100 iterations. Here, LastPass customers can see how many PBKDF2 iterations are currently running on their accounts.
Everyone ought to create an account on Have I been Pwned? regardless of whether or not they use LastPass. to make sure they are informed as soon as possible of any breaches that may affect them.
Customers of LastPass should also be on the lookout for phishing emails and phone calls claiming to be from LastPass or other services and requesting sensitive data. Other scams that take advantage of their compromised personal data include these types of scams. Additionally, the company offers tailored guidance to business clients who have implemented the LastPass Federated Login Services.
- Log in to post comments